WordPress Security Tips
What is Security?
Fundamentally, security is not about perfectly secure systems. Such a thing might well be impractical, or impossible to find and/or maintain. What security is though is risk reduction, not risk elimination. It’s about employing all the appropriate controls available to you, within reason, that allow you to improve your overall posture reducing the odds of making yourself a target, subsequently getting hacked.
Table of contents
1. Should not use admin as a username
2. Use a less common password
3. Add Two-Factor Authentication
4. Employ Least Privileged principles
5. Hide wp-config.php and .htaccess
6. Use WordPress security keys for authentication
7. Disable file editing
8. Limit login attempts
9. Be selective with XML-RPC
10. Hosting & WordPress security
11. Stay up-to-date always
12. (Free) plugins & themes
13. Understand File and Folder Permissions
14. Backup, Backup, Backup
WordPress itself has a list on WordPress Security Tips you might want to read. Of course, some of the things in that list will be repeated in the article below. We prefer a more hands on list and direction, that’s why we decided to write this article.
Should not use admin as a username
This is perhaps the easiest baseline step for WordPress Security you can take as a WordPress user. It costs you nothing, and the install makes it really easy to do. A majority of today’s attacks target your wp-admin / wp-login access points using a combination of admin and some password in what is known as Brute Force attacks. Common sense would dictate that if you remove admin you’ll also kill the attack outright.
The argument exists that the attacker can still enumerate the user ID and Name and can in some instances pull the new username. There is no denying this. Remember though, Security is not about risk elimination, it’s about risk reduction.
For the everyday, automated Brute Force attack, removing the default admin or administrator username will already help a lot. You’re at least making it a bit harder for the hacker to guess the username. For the sake of clarity, understand that when we say “admin” we are speaking specifically to the username only and not the role.
Simply create a new user in WordPress at Users > New User and make that a user with Administrator rights. After that, delete the admin user. Don’t worry about the post or pages the admin user has already created. WordPress will nicely ask you: “What should be done with content owned by this user?” and give you the option to delete all content or assign it to a new user, like the one you have just created.
Use a less common password
An easy thing to remember is CLU: Complex. Long. Unique.
This is where tools like 1Password and LastPass come into play, as they each have password generators. You type in the length, and it generates the password. You save the link, save the password, and move on with your day. Depending on how secure I want the password to be, I usually set length of the password (20 characters is always right) and decide on things like the inclusion of less usual characters like # or *.
‘123456’ isn’t a password. ‘qwerty’ is like writing your security code on your bank card. ‘letmein’; seriously? Shame on you. Even ‘starwars’ made the 2015 list of 25 most used passwords. Remember, you’re never as unique as you think you are…
Add Two-Factor Authentication
Even if you’re not using ‘admin’ and are using a strong, randomly generated password, Brute Force attacks can still be a problem. To address this, things like Two-Factor Authentication are key to helping to reduce the risk of such attacks.
The essence of two-factor authentication for WordPress Security is exactly as implied in the name, two forms of authentication. It’s the recognized standard today for enhanced security at your access points. You are already using two-factor authentication for Gmail, Paypal, and the works (at least you should be), why not add it to your WordPress Security toolkit as well
. Ipstenu (Mika Epstein) did an article on the subject you might want to read: Two Factor Authentication.
There is a plugin for that: Google Authenticator. An alternative that takes a slightly different approach for the same purpose is the Rublon Plugin.
Employ Least Privileged principles
The WordPress.org team put together a great article in the WordPress Codex regarding Roles and Capabilities. We encourage you to read it and become familiar with it because it applies to this step.
Concept of Least Privileged is simple, give permissions to:
> those that need it,
> when they need it and
> only for the time they need it.
If someone requires administrator access momentarily for a configuration change, grant it, but then remove it upon completion of the task. The good news is you don’t have to do much here, other than employ best practices.
Contrary to popular belief, not every user accessing your WordPress instance needs to be categorized under the administrator role. Assign people to the appropriate roles and you’ll greatly reduce your security risk.
Hide wp-config.php and .htaccess
It’s actually really simple, especially when you are using Yoast SEO for WordPress > Tools > File Editor to edit your .htaccess.
For better WordPress Security, you’d need to add this to your .htacces file to protect wp-config.php:
<Files wp-config.php>
order allow,deny
deny from all
</Files>
That will prevent the file from being accessed. Similar code can be used for your .htacces file itself, by the way:
<Files .htaccess>
order allow,deny
deny from all
</Files>
You can do it easily.
Use WordPress Security keys for authentication
Keys and Salts work in conjunction with each other to protect your cookies and passwords in transit between the browser and web server. These authentication keys are basically set of random variables, used to improve security (encryption) of information in cookies. Changing this in wp-config.php can be simply done by getting a new set of keys here and add these. These keys change on a refresh of that page, so you’ll always get a fresh set.
Disable file editing
If a hacker gets in, the easiest way that he could change your files would be to go to Appearance > Editor in WordPress. To lift your WordPress Security, you could disable writing of these files via that editor. To do this Again, open wp-config.php and add this line of code:
define(‘DISALLOW_FILE_EDIT’, true);
But still you will be able to edit your templates via your favorite FTP application, you just won’t be able to do it via WordPress itself.
Limit login attempts
The attacks like a Brute Force attack, target your login form. Specifically for WordPress Security, the All in One WP Security & Firewall plugin has an option to simply change the default URL (/wp-admin/) for that login form.
You could also limit the number of attempts to login from a certain IP address. There are several WordPress plugins to help you to protect your login form from IP addresses that fire a multitude of login attempts your way.
Be selective with XML-RPC
XML-RPC is an application program interface (API) that’s been around for a while. It’s used by a number of plugins and themes, so we caution the less technical to be mindful how they implement this specific hardening tip.
While functional, disabling can come with a cost. Which is why we don’t recommend disabling for everything, but being more selective on how and what you allow to access it. In WordPress, if you use Jetpack you’ll want to be extra careful here.
There are lots of plugins that help you be very selective in the way you implement and disable XML-RPC by default.
Hosting & WordPress Security
Hosting companies simply see your website differently. There is no simple rule to decide on your WordPress hosting company. But the choice of a hosting company does matter when optimizing your WordPress Security.
All most Every article written on hosting or hosting companies seems to start by telling you that the cheapest one is probably not the best one. Most cheaper hosting plans won’t have support to help you out with a hacked site. These plans include little to secure your website, like for instance set up a Website Firewall. Shared hosting, for instance, does imply that your hosting server is also populated with other websites. These might have security issues of their own, which in turn might affect your own website’s security as well.
Be mindful of host account
One of the biggest challenges with hosts is in their account configuration for website owners. Website owners are allowed to install and configure as many websites as they want, and this fosters “soup kitchen”-like environments.
This is challenging because, in many instances, a website is compromised via a concept known as cross-site contamination in which a neighboring site is used as the attack vector. The attacker penetrates the server, then moves laterally into neighboring sites on the server.
Best way to account for this is to create two accounts, one which you treat as a production environment – only live sites are published – and a staging one, in which you put everything else.
Stay up-to-date always
Staying up-to-date is an easy statement to make, but for website owners in the day-to-day, we realize how hard this can be. Our websites are complex beings, we have 150 different things going at any given time, and sometimes it’s difficult to apply the changes quickly.
Updates need to extend beyond WordPress core. The same study shows that a very large percentage of the website hacks came from out-of-date, vulnerable, versions of plugins.
This can be compounded in really complex environments in which dependencies make it so that backups can’t be achieved. This is why we personally employ Sucuri’s Firewall. This firewall virtually patches and hardens our website at the edge. It gives us the time we require to go back and apply updates in a more reasonable time frame, allowing us to test in our staging environments first, and only then push to production.
(Free) plugins & themes
WordPress have a tendency to apply themes and plugins at will to their posts. Unless you’re doing this on a test server for the sole purpose of testing that theme or plugin, that makes no sense, especially not with reference to WordPress Security. Most plugins and a lot of themes are free, and unless you have a solid business model to accompany these free giveaways. If a developer is maintaining a plugin just because it’s good fun, chances are he or she did not take the time to do proper security checks.
How to pick the right plugin
Let us focus on the basics of plugin selection here. As explained above, free plugins and themes could be a possible vulnerability. When adding a plugin (or theme for that matter), always check the rating of that plugin. WordPress.org shows ratings, but one five star rating won’t tell you anything, so also check the number or ratings. Depending on the niche, a plugin should be able to get multiple reviews. If more people think a plugin is awesome and take the time to rate it, you could decide to use it too.
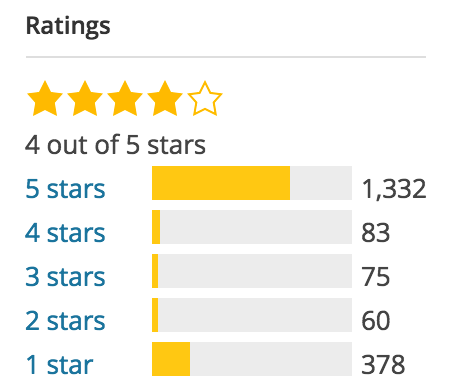
Another thing you want to check is, If a plugin hasn’t been updated for two years, WordPress will tell you that. That doesn’t mean it’s a bad plugin, it could also mean there hasn’t been a need to update it, simply because the plugin still works. The ratings will tell you that, and the compatibility with the current WordPress version, which is also listed on the plugin page at wordpress.org.
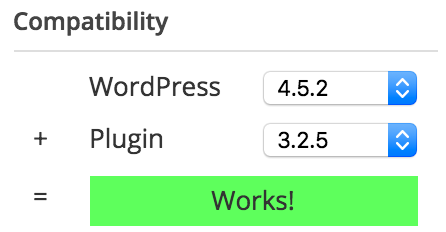
Based on these ratings and compatibility, you could pick your plugins less random and have a larger chance of some kind of security being added.
Understand File and Folder Permissions
In the vast majority of cases, you shouldn’t need to mess around too much with WordPress defaults but it’s worth your while having at least a cursory understanding of file permission modes in general.
The two most common modes you will come across are 644 and 755. These are basically categories that determine the set of rules that govern each file or directory (i.e. who can read, open or modify files).
Files and directories categorized under the 644 mode can be read and written to (this is UNIX-speak for modified in any way) by their owner (the user on the server who created them) but only read by everyone else. This is the ideal setting for many types of files.
The 755 mode meanwhile is mostly used for folders since it allows all users to change into that directory. You’ll occasionally come across plugins that require certain folders to be set to 755.
File and folder permissions can be a head-melting topic if you are new to it but, if you remember nothing else, bear in mind that you should always avoid setting a permission mode to 777 – – even if a plugin explicitly asks you to – unless you know exactly what you’re doing.
This mode is basically a big no-no since it grants complete access to absolutely any user, allowing them to read, write to or delete directories at will and potentially cause all sorts of problems.
Backup, Backup, Backup
“Even through I walk though the valley of the shadow of death, I will fear no evil, for I have dutifully performed backups.”
Backups are such a simple yet crucial part of site security they should be preached as gospel.
In the unfortunate event of a security breach – catastrophic or otherwise – you’ll be enormously thankful you had adequate backups. Fail to get them in place in advance and the road back could be long and painful.
The only potential downside here is if you’re only performing backups semi-regularly where you risk potential data loss if backups are out of date. A weekly or bi-weekly backup should be more than enough for most websites and these can be automated through plugins so you don’t actually have to remember to perform them manually.
If you’re worried about maintaining a huge library of unnecessary backups, well, that could happen. But then again it’s 2015 – online and offline storage space are both ridiculously cheap and the cost involved is well worth the peace of mind it brings. Plus, you can always rotate the oldest snapshots out of storage once a set amount of time has passed to save on space.
Like Us on Facebook:
Follow Us on Linkedin:
If you are looking for a web design dubai based company for your website design work, then you must contact us for a better web design deal. Choosing your web design dubai based company really matters for your company web design work.








